USING DNS RECORDS
WEB DATA INVESTIGATION 101
When performing a web investigation, it’s important to understand how the pieces of data fit together. Someone who fully understands how the Internet works, by analyzing the overall picture, will be able to achieve a much better result. In many cases, it’s possible to see that different aspects of online activity are actually related in ways, which may not have been anticipated in the beginning.
An unfriendly actor who’s been very good at covering their tracks with bad domains might just host a family blog on the same web server, for example. Such traces can be identified from bits of data acquired from outside the investigation.
That is why it’s necessary to pay attention to the DNS data and be aware of using DNS records.
What is DNS
The Domain Name System (DNS) is like the phonebook of the Internet. People access data online through domains, such as www.mywebsite.com, but Internet browsers only read Internet Protocol (IP) addresses, which are strings of numbers. So, the job of DNS is to interpret a domain name and redirect to an IP address which enables a browser to find and then load the correct Internet page.
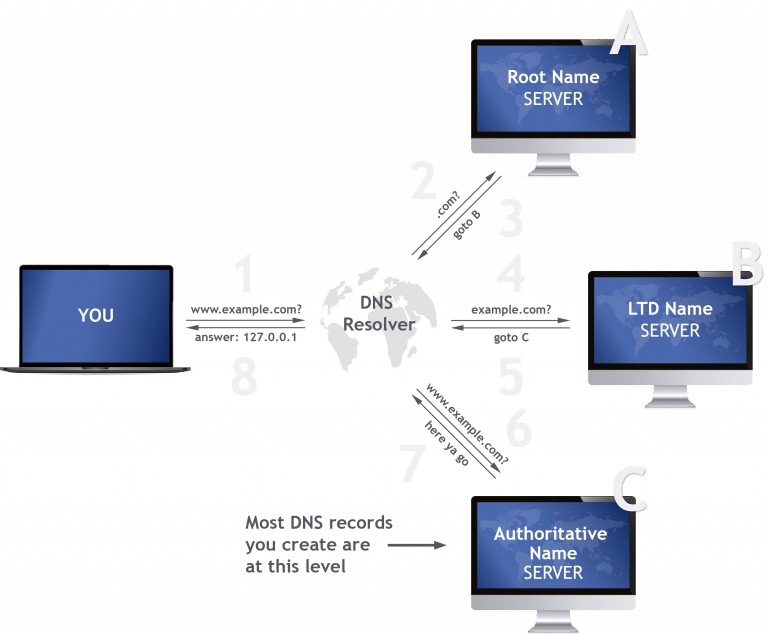
Let’s say a user wants to view a page on “mywebsite.com”, the web browser needs to find the associated IP address and this is performed using a DNS lookup – otherwise known as a DNS zone check. It’s directed to the DNS server that manages the DNS zone for that hostname, also known as the authoritative name server. The IP address or other data is then provided by the authoritative name server which has performed a DNS lookup and resolved that domain name.
The DNS root is at the top, and then split up into zones, like a hierarchical tree. Starting at the top a DNS zone extends down into subdomains with multiple subdomains managed by one entity. Its main purpose is to be used as an administration function allowing the control of DNS components, such as authoritative name servers.
Let’s say a user wants to view a page on “mywebsite.com”, the web browser needs to find the associated IP address and this is performed using a DNS lookup – otherwise known as a DNS zone check. It’s directed to the DNS server that manages the DNS zone for that hostname, also known as the authoritative name server. The IP address or other data is then provided by the authoritative name server which has performed a DNS lookup and resolved that domain name.
DNS records
Each DNS server has a DNS zone file, a plain text file stored locally that details the actual zone and which contains all the records for every domain within the zone. Zone files must always begin with a unique record, and are extremely useful for investigations because they detail important information including contact information for the zone administrator. A typical zone file has the following format:
- Name: alphanumeric identifier of DNS record. Can be blank, and inherits its value from the previous record.
- TTL (time to live): Specifies how long the record should be kept in the local cache of a DNS client. If not specified, the global TTL value at the top of the zone file is used.
- Record class indicates namespace—typically IN
- Record type is the DNS record type—for example an A record maps a hostname to an IPv4 address, and a CNAME is an alias which points a hostname to another hostname.
- Record data has one or more information elements, depending on the record type, separated by a white space.
How DNS records can be useful for web data investigations
It’s possible to find websites that belong to one owner or interconnected websites using DNS information, specifically IP addresses. This is not always 100 percent reliable, however, as websites that belong to many different owners can have the same IP address in shared hosting scenarios. Even so, sites that have the same IP address often belong to a single owner and it’s usually a fairly good indicator.
Also, it’s possible to locate shared Name Servers and the combination of those two things – shared IP address and Name Server – can significantly help the investigation.
All domains under a single IP can be checked, as well as all other domains hosted on the same Name Server. Reverse Name Server and Reverse IP Lookups can be effective methods to map domains together in the case where there is a common IP address or Name Server. This can be used both as a way to validate connections between unauthorized domains as well as to eliminate possible ‘false positives.’
The example
Suppose when conducting HTML tags research with the Domain Research platform from DomainCrawler, we find a website that looks dubious- big discounts on luxury goods, social media buttons that don’t function, or other such warning signs. There is a high possibility then that this is a fake webshop.
We go to the DNS record and by clicking on A record we can conduct a Reverse IP lookup.
In this example, 69 domain names share the same IP address with our dubious website.
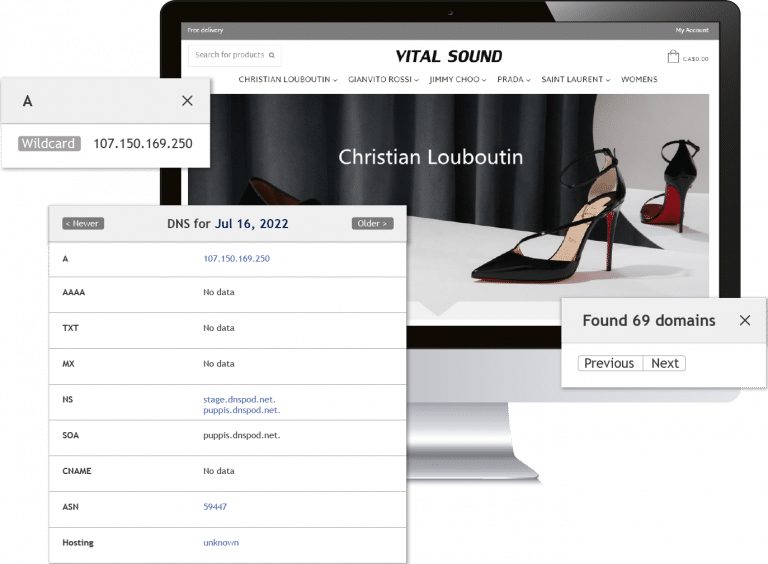
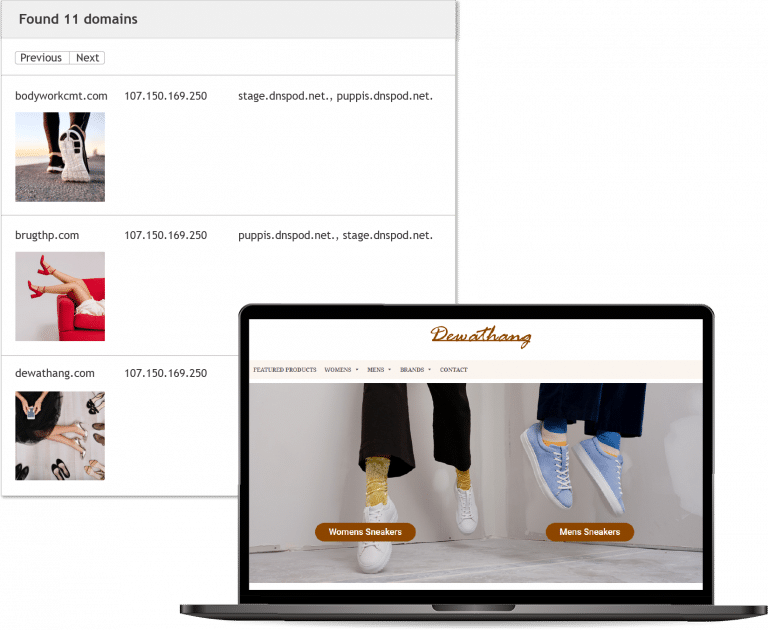
Then by including the Name Server record in order to narrow the search the result set can be shortened to 11 domains.
Immediately we can see that 2 or more in this list are webshops that warrant a much closer look.
In a very short time therefore, it’s possible to scan the entirety of the Internet and gain some insightful results. Of course, for tackling extensive illegal trade, it’s just the beginning of the process but this is how is can be somewhat simplified.


